Security is always a concern for every company especially as more data is being saved off premises and onto the cloud. The Microsoft Security, Compliance, and Identity Fundamentals certification (SC-900) is a great entry point to Microsoft security, compliance, and identity concepts. It is essential to know how to keep information secure regardless of if it’s on-premises or being hosted on the cloud.
Zero Trust Methodology
The Zero Trust Methodology assumes that everything is on an open, untrusted network. It is the principle of “Trust no one, verify everything”. In practice, this means assume a password isn’t strong enough and enforce multi-factor authentication.
The Zero Trust Methodology has three core concepts:
Verify Explicitly: Always authenticate and authorize based on various data points such as location, device, data classification, etc.
Least Privileged Access: Give the least amount of access to an individual for them to be able to perform their job duties.
Assume Breach: Segment various portions of your environment such as networks, users, and applications. Use encryption to protect data and use analytics to detect threats, anomalies, and to improve overall security.
After applying the three core concepts to your environment, the Zero Trust Methodology has six foundation pillars to help provide end-to-end security. These six pillars are:
Identities: This may be users or devices. When an identity attempts to access a resource, it must be verified and follow the least privileged access principle.
Devices: Monitor devices for health and compliance. This is an important aspect of security as it can create a large attack surface as data flows from the device to on-premises or the cloud.
Applications: This pillar includes managing permissions and access. Applications are the way data is consumed. This pillar includes finding all the applications that are used, it is sometimes called Shadow IT as not all applications are centrally managed.
Data: Security is ultimately about protecting data. Data should be classified, labeled, and encrypted based on its attributes. This is to ensure that data remains safe when it leaves applications, devices, infrastructure, or networks that the organization controls.
Infrastructure: This represents a threat vector. Assess your version, configuration, least privileged access, and use telemetry to detect attacks and anomalies to improve your overall security. This allows you to automatically block or flag risky behavior and take action.
Networks: This should be segmented including deeper in-network segmentation. Configure real-time threat protections, end-to-end encryption, monitoring, and analytics to manage your network security.
Applying all the concepts and principles from the Zero Trust Methodology will help reinforce your company’s security policies.
Shared Responsibility Model
This model identifies which security tasks are handled by the cloud provider and which are handled by you. If your company is completely on-premises, your company is 100% in charge of managing security and compliance. With cloud-based technology, this responsibility is split between the cloud provider and organization. This responsibility varies depending if it is Infrastructure as a Service (IaaS), Platform as a Service (PaaS), Software as a Service (SaaS), or your on-premises infrastructure. The Shared Responsibility model helps make this clear. When you begin to move data to the cloud, some of the responsibility shifts over to the cloud provider and some to your organization. The diagram below helps describe the responsibility between the cloud provider and the organization based on where the data is held.
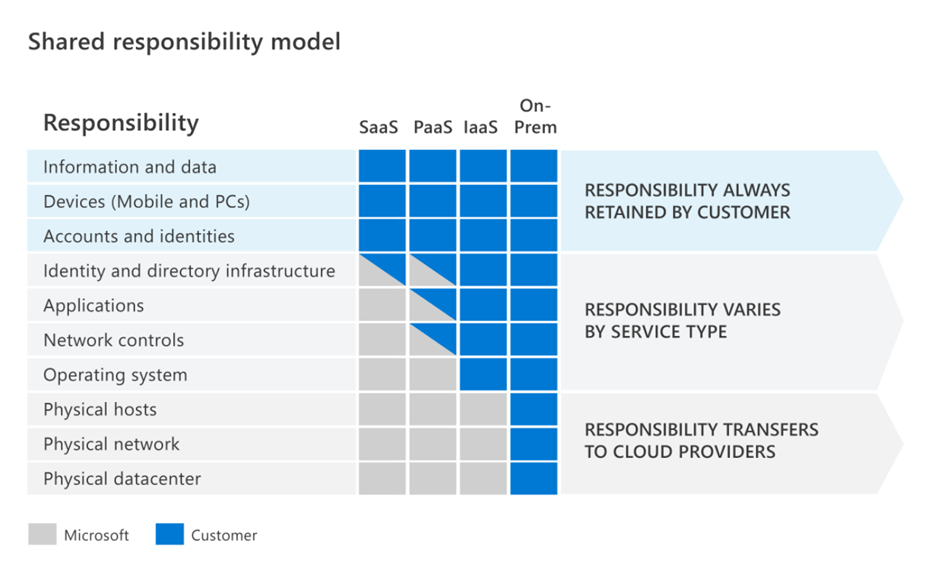
On-Premises: The organization is 100% responsible for everything from physically security to encryption of sensitive data.
IaaS: This requires the least management from the cloud provider. You are using cloud provider’s computing resources/infrastructure which makes them responsible for physical components, such as computers, physical data center, and the network. However, the organization is responsible for software components such as operating systems, network controls, applications, and data.
PaaS: A PaaS provides an environment for developing, testing, and deploying software applications. The main goal for a PaaS is to allow you to create applications quickly without worrying about the underlying infrastructure. This allows the organization to only be responsible for their applications and data while the cloud provider is responsible for hardware and operating systems.
SaaS: This is typically completely managed by the cloud provider. It’s usually licensed with a monthly or annual subscription. This usually requires the least amount of responsibility for the organization, as the cloud provider is responsible for everything besides data, devices, and identities.
Defense in Depth
Defense in depth uses a layered approach to security instead of relying on a single defense. This strategy uses a series of mechanisms to slow an attack. Each layer of security control provides protection so if one layer is compromised the subsequent layer will prevent an attacker from accessing the data.
Here are some examples that layers may include:
Physical: Limiting access to datacenters
Identity and Access: Security controls to limit access to infrastructure such as conditional access or multi-factor identification.
Perimeter: Security that filters large-scale attacks before they can cause a denial of service for users.
Network: Network segmentation and network access controls to limit communication between resources
Compute: layer security for example securing access to virtual machines by closing certain ports
Application: Security to make sure applications are secure and free of vulnerabilities
Data: Controlling who can manage access to data and utilizing encryption to protect data
Confidentiality, Integrity, Availability (CIA)
This is a way of thinking about security trade-offs. This model is common to all security professionals.
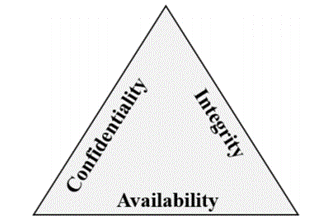
Confidentiality: This refers to keeping sensitive data confidential. Organizations can encrypt data to keep it confidential, but the encryption keys also need to be kept confidential. This is the most visible part of security as we can see which sensitive data needs to be kept confidential.
Integrity: Integrity is having confidence that data hasn’t been tampered with or altered. For example, if you store data in a database, you want to make sure you can receive the same data that you stored. You can encrypt data to keep in confidential, but you must then be able to decrypt the data.
Availability: Availability is making the data available for those who need it. It is essential for an organization to keep customer data secure but must be available for the employees who need to access the data. It may be more secure to encrypt the data, but employees must be able to decrypt the data.
Common Threats
There are many types of security threats that aim to have various end goals such as stealing data, extorting money, or to disrupt normal operations. This is a quick brief overview of commonly seen security threats.
Data Breach: A data breach is where data is stolen from an organization. This can include various types of data including personal. This breach usually occurs from SQL injections, phishing, malware designed to steal passwords/bank details, etc.
Ransomware: Typically, malware that can cause damage and disrupt normal use of devices. This can give attackers unauthorized access which can allow them to use system resources, lock you out of your accounts, and ask for a ransom. Ransom is a type of malware that encrypt files and prevents access to the data until a ransom is paid.
Dictionary Attack: This is an attempt to steal an identity by using a large pool of known passwords. This is also known as a brute force attack.
Disruptive Attack (DDoS): A Distributed Denial of Service (DDoS) attempts to exhaust application resources making it unavailable for users. This typically targets an endpoint that is publicly reachable through the internet.
Malware: There are multiple types of malwares. For example, Trojans are a common type of malware that is typically spread through downloading a file. They often use the same name as real and legitimate applications.
These are just a few examples of commonly seen threats. This is an area that is continuing the evolve and make organizations adapt their security to safeguard against threats.
Encrypting and Hashing Data
One way to protect yourself from threats is to encrypt sensitive data. Encryption is a process of making data unreadable and unusable to unauthorized users. To access the data, it must be decrypted by a key. There are two top-level types of encryptions which are symmetric and asymmetric. Symmetric encryption uses the same key to decrypt and encrypt data. Asymmetric, on the other hand, uses to different keys to decrypt and encrypt data. This involves a private and public key, either key can encrypt the data, but to decrypt the data you must use a paired key. This is common with technologies such as Transport Layer Security (TLS).
Encryption at Rest: Data at rest is data stored on a physical device such as a server, database, or storage account. Encryption at rest makes the data unreadable without keys to decrypt it.
Encryption in Transit: This helps keep data secure as it moves from one location to another, encrypting the data from outside observers and limiting risk of exposure. This can be handled by several different layers or could be done by encrypting the data at the application layer. HTTPS is an example of encryption in transit.
Hashing
Hashing is a way of using an algorithm to convert text into a unique fix-length hash value. Each time the data is hashed using the same algorithm, the same hash value is created. This can be used as a unique identified for the data. This is different of encryption as it doesn’t use keys and the hash value isn’t used to decrypt data back to the original. This is typically used for storing passwords. It is more secure than saving passwords in plain text, but hashing algorithms are commonly known to hackers since hash functions produce the same input and output. To mitigate risks from hackers, passwords are often “salted”. This refers to adding a fixed-length random value to the input hash functions to create a unique key for every input. This leads the data to be more secure as hackers often do not know the salt value.
Cloud Adoption Framework (CAF)
This section describes Microsoft’s Cloud Adoption Framework for Azure. This consists of documentation, implementation guidance, best practices, and tools designed to implement strategies in their Azure environment. CAF has been designed based on best practices from Microsoft employees, customers, and partners. It is based on proven and consistent methodology for cloud technologies.
CAF Lifecycle
Below are steps that are part of the Cloud Adoption Framework:
Strategy: define business justifications and expected outcomes
Plan: align adoption plans to business outcomes
Ready: Prepare cloud environment for expected changes
Adopt:
Migrate: Migrate and modernize workloads
Innovate: Develop new cloud or hybrid solutions
Govern: Govern environment and workloads
Manage: Operation management for cloud and hybrid solutions
Conclusion
There are many steps and factors when it comes to security. The multiple guiding principles, methodologies and knowledge of common threats can help keep your organization secure from threats in the future. Hopefully this knowledge can provide a base on keeping your data and environment secure if it’s either in the cloud or on-premises
Sources:
- Zero Trust Methodology: https://www.microsoft.com/en-us/itshowcase/implementing-a-zero-trust-security-model-at-microsoft
- Share Responsibility Model: https://docs.microsoft.com/en-us/azure/security/fundamentals/shared-responsibility
- Defense in Depth: https://docs.microsoft.com/en-us/azure/security/fundamentals/overview
- Cloud Adoption Framework: https://docs.microsoft.com/en-us/azure/cloud-adoption-framework/overview
